Process Behavior API
With this API you can detect Windows malware process behaviors.
Consider this API as a
cloud Windows process behavior detection API that can be included into any security software
to add an additional process safety check. It can be used also to scan logs of processes executed in a Windows system
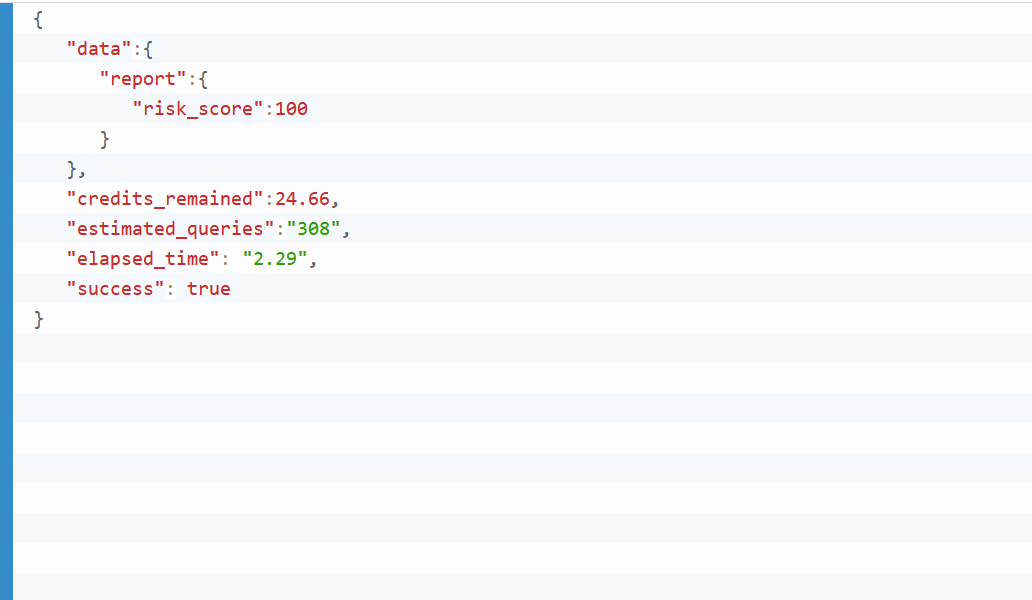
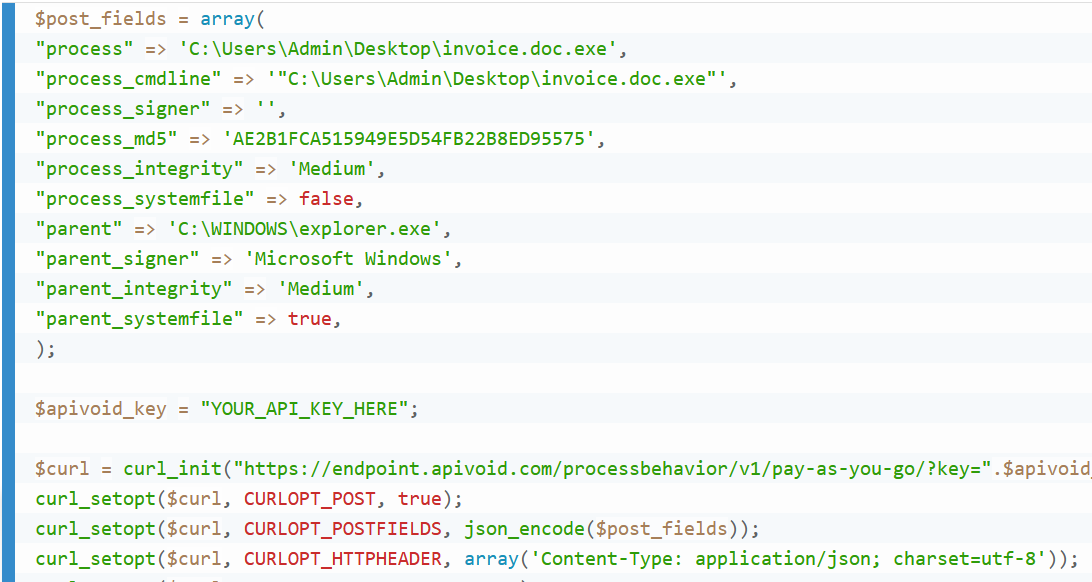
to spot suspicious processes behaviors. You just need to submit the process details (process, command-line, signer, parent, etc) and
our API will scan the process
behavior
and provide a risk score from 0 (good) to 100 (bad).
Register and get 25 free API credits