🚀 Experience the new and improved APIVoid! Check out what's new
Strengthen your incident response with our powerful IoC validation APIs. Designed to verify the authenticity and relevance of indicators of compromise (IoCs), such as IPs, domains, URLs, and email addresses, our APIs ensure you act on accurate and trustworthy data.
IP Address: 93.174.95.106
Checking reputation...
IP Address: 2001:df7:3c00:800a::446:34dc
Checking reputation...
Domain: roupasales(.)shop
Checking reputation...
Email: a1u8e3ka@yopmail(.)com
Checking reputation...
Phone: +447457413341
Checking reputation...
Domain: domicileposte(.)net
Checking reputation...
Domain: moncler(.)com
Checking reputation...
IP Address: 206.220.175.2
Checking reputation...
Domain: ver1fy-password(.)top
Checking reputation...






By automating the validation process, you can reduce the manual effort of security analysts and focus on what truly matters — mitigating threats quickly and effectively. Whether it’s identifying malicious domains or validating suspicious IP addresses, our APIs integrate seamlessly into your existing incident response workflows, enhancing their efficiency and precision. Improve collaboration, reduce response times, and increase confidence in your security decisions by relying on out powerful threat intelligence APIs.
Check the safety reputation of an IPv4 or IPv6 address using multiple IP address blacklist services.
Check the reputation of a domain (e.g google.com) using multiple domain blacklist services.
Check the safety reputation of an email address, detect temporary emails and suspicious emails.
Validate and normalize a phone number, get location, carrier and line type, detect invalid and fake numbers.
Check the safety reputation and risk score of an URL using unique URL security checks.
Obtain a "trust score" of any website, useful to spot potentially fraudulent and insecure web shops.
Account and API Security
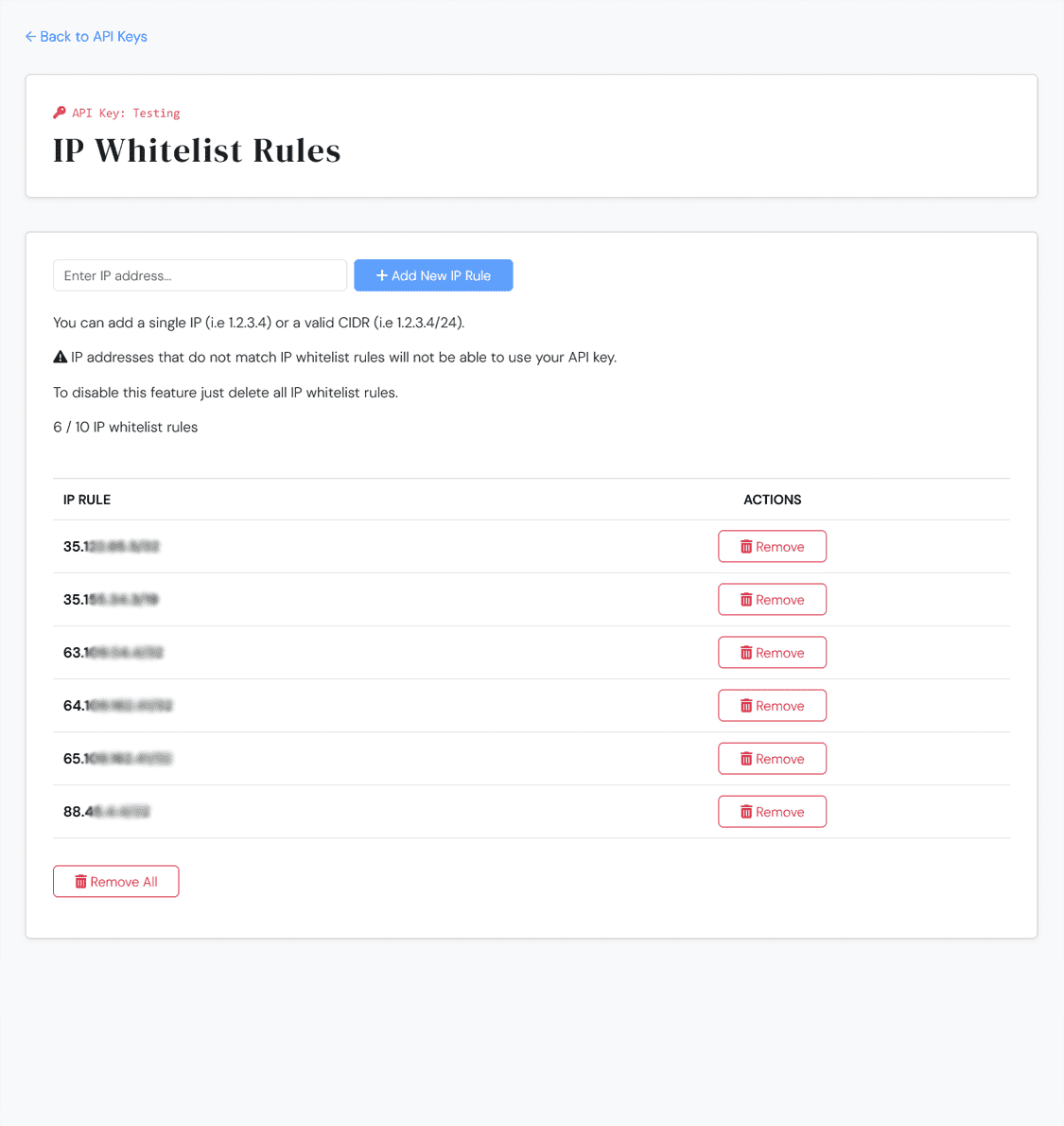
Data sent on the Dashboard account and on our API services is always encrypted (on frontends and backends). We provide options to secure your account with 2FA and your API keys with IP CIDR whitelist.
All traffic on our API services is safely encrypted in transit with HTTPS SSL (TLSv1.2+) encryption.
Protect your API keys by allowing only trusted CIDR IP addresses and block unknown IP addresses.
You can enable 2FA authentication via Google Authenticator to additionally protect your account.
Your account data is encrypted in transit and at rest by default within Google Cloud Platform.
Key Service Features
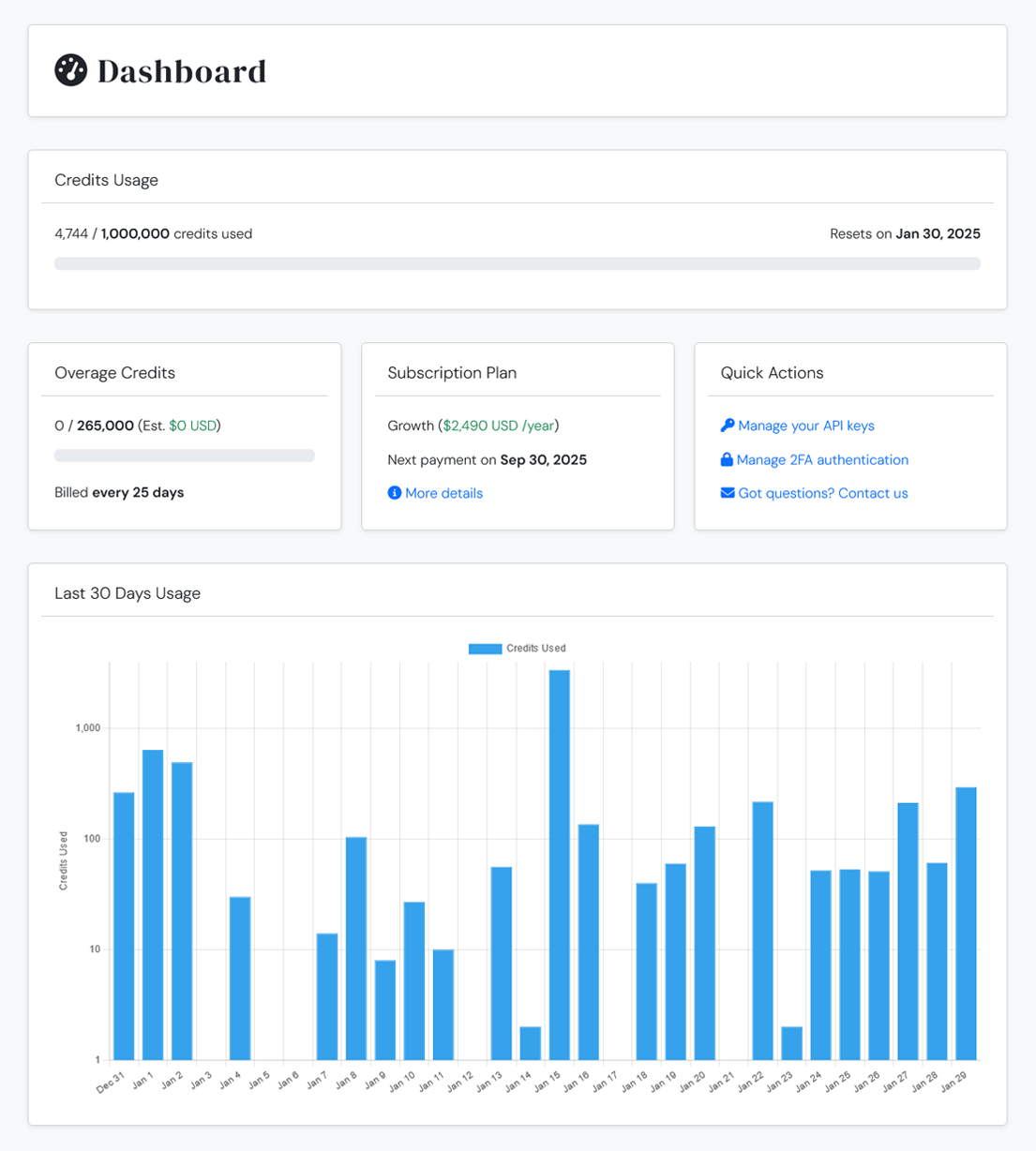
With our service you can: use one or more APIs within your subscription, manage multiple API keys, customize the overages and more. Choose the right plan with the help of our pricing calculator.
Within your subscription you have access to all our 20+ (and growing) threat intelligence APIs.
We provide automated monthly or yearly subscription plans. With a yearly plan you get 2 months free.
Starting with the Startup plan, you can enable overages option to extend your monthly plan credits.
Based on your plan, you can manage multiple API keys (such as one for Production and one for Testing).
Create your account, pick a subscription plan, and make your first API call instantly with your API key—simple as that!
Get started now